Article Summary:
- The phrase “social engineering” is used to describe a wide variety of scamming tactics that hackers use when interacting with their potential victims. Often times, unsuspecting people are duped into divulging critical information or committing security blunders.
- Scammer attacks generally fall into one of these five categories: baiting, scareware, pretexting, phishing, and spear phishing.
- The four tips to avoid being scammed are: Never open attachments or emails from unknown sources. Use multifactor authentication. Be skeptical of alluring offers. Keep your antivirus and antimalware programs updated.
Well before the Great Information Age began in the late 20th century, our civilization was skilled at creating mountains of data. If you ever have the opportunity to visit the Smithsonian in Washington D.C. or the British Museum in London, you’ll be amazed by how much human data we’ve collected over the millennia. It’s truly astounding.
Today however, data collection is no longer measured in mountains, but in bytes… and it’s bigger than you could ever imagine. In fact, there are 400,000 bytes of data for EVERY single grain of sand on earth… and this number continues to grow at a dizzying pace.
Fun fact: There are 400,000 bytes of data for every grain of sand on Earth. pic.twitter.com/1jMsjNNjck
— DataCamp (@DataCamp) October 29, 2021
Moreover, inside this vast amount of data stored all over the world are records of our Personal Identifiable Information or PII. Individuals and businesses leave behind digital footprints of their activity on the internet (names, addresses, birthdates, family information, work history, educational background, bank records, social security numbers, passwords, etc.). Despite the herculean efforts to keep this information secure, data breaches happen on a daily basis. Today, our PII is often exposed and sold on the dark web to hackers and scammers. Your PII is a gold mine in this latest sequel of the Wild West gold rush.
By investigating your online activity, scammers build a personal profile of your identity. They dig deep into this treasure trove to engineer their sophisticated attacks. It’s important to realize, as you move about the day unaware of their activities, they are working feverishly to hijack your identity. What’s the payoff? Specifically, they want to gain access to your bank accounts and other sensitive information, either to steal your hard-earned money or launch a variety of extortion campaigns.
But, consider the good news! You can protect yourself by vigilance, understanding their schemes, and implementing personal safeguards. Here’s what you need to know!

Social Engineering: Scammers And Their Victims
The phrase “social engineering” is used to describe a wide variety of scamming tactics that hackers use when interacting with their potential victims. Often times, unsuspecting people are duped into divulging critical information or committing security blunders.
These attacks usually involve many phases. The scammer first investigates the victim in preparation for the attack. He or she studies background information like potential points of entry and lax security measures. Next, the attacker makes an effort to win over the victim’s confidence and trust. The use of psychological manipulation is a common tactic. They may offer incentives for the victim to break their security protocols, such as: disclosing confidential information or allowing access to vital resources.
Social engineering relies on humans making mistakes rather than flaws in software and operating systems. Every business leader should understand the risks and hazards here. User errors are hard to predict but often happen during times of high stress loads, distraction, or lack of sleep. All it takes is one click to open the door to a malware-based intrusion.
Social Engineering: Scammers And Their Tactics
Broadly speaking, social engineering can occur in any place where people interact. It’s a good idea to learn how scammers operate so that you can protect yourself and your financial interests. The five most typical attacks are listed below.
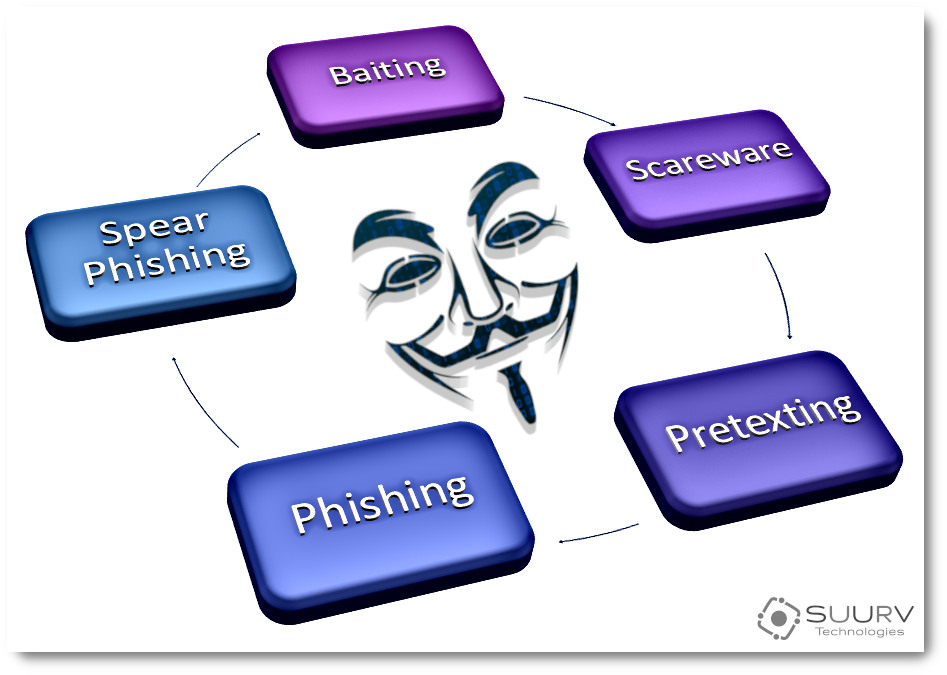
First: Baiting
Imagine an employee walking through their parking garage one morning. They discover an abandoned thumb drive on the pavement. Curious, they pick it up and investigate. The drive bears their company logo and a label marked, “Payroll.” They rush back to their desk and insert the drive into their computer. That’s when disaster strikes. Every hard drive on the network is now encrypted. There are many incidents like this where employees inserted thumb drives in company computers that were strategically placed in bathrooms, elevators and breakrooms.
Scammers use baiting strategies to spark a victim’s interest and manipulate their emotions. The goal is to trick their mark to step into a trap. The bait may appear in the form of false promises, offers that are too good to be true, or a passionate plea for help. If successful, the scammer can steal their personal information or infect their computers with malware.
Other common baiting scenarios often occur online. There may be an attractive advertisement that directs visitors to a harmful website, or invite them to download free software that is laden with malware. One thing is for certain, these scams get more creative every year.
Second: Scareware
Scareware bombards victims with bogus threats and misleading alarms, e.g., “Your computer is infected with a virus.” Users are tricked into believing that they need to react immediately by following the instructions. This leads them to install software that is, in fact, real malware. Other names for scareware include: fraudware, deception software, and rogue scanning software.
Additionally, spam emails that provide false alerts or urge recipients to purchase useless or hazardous services are a common way for scareware to spread.
Third: Pretexting
Here, an attacker gathers data by telling a string of deftly constructed falsehoods. The con is frequently started by a perpetrator who poses as someone who needs the victim’s private information to complete a crucial assignment.
The scammer typically begins by gaining the victim’s trust and appearing authoritative. They may claim to be a coworker, police officer, bank or tax official, or any person with the power to know something. Through queries that are allegedly necessary to verify the victim’s identification, the pretexter collects sensitive personal information.
This fraud is used to obtain all kinds of important data and records, including: social security numbers, individual addresses, phone numbers, phone records, dates of staff vacation, bank records, and even security data pertaining to a physical plant. Unfortunately, no business large or small is immune from these types of attacks. For instance, consider what happened to Uber recently.
Update: a person claiming responsibility for the Uber hack tells the NYT that he is 18, got in through social engineering an employee’s password, and hacked the company because it had weak security. https://t.co/h3k7H9lpSo pic.twitter.com/TZ8aDrNyQQ
— Kevin Roose (@kevinroose) September 16, 2022
Fourth: Phishing
Phishing scams are one of the most common forms of social engineering attacks. They usually begin with an email or text message that is designed to make their victims feel rushed, curious, or afraid. The victim is prompted to divulge private information, click on links to nefarious websites, or open attachments that are infected with malware.
A common scenario might be an email or text message sent to subscribers from an online service that reads, “Your account is in violation of our policies.” They need to take quick action and change the password or their account will be frozen. The email or text message contains a link to a malicious website that looks almost exactly like its official counterpart. It requests the unwary user to input their existing login information and create a new password. This information is delivered to the attacker when the form is submitted.
Fortunately, given that phishing campaigns send almost similar messages to all users, mail servers with access to threat sharing systems will have an easier time identifying and stopping them.
Fifth: Spear Phishing
In this more focused variation of the phishing scam, an attacker will choose certain people or companies to target. Then, in order to make their attack less obvious, they modify their communications based on the traits, positions held, and contacts of their victims. All things considered, spear phishing is far more difficult to carry off and might take weeks or even months to complete. If executed with expertise and finesse, they’re significantly more difficult to detect and have higher success rates.
Always verify the sender of any email. It pays to be suspicious if something seems off. Scammers often pose as the company’s IT department or colleagues during spear phishing campaigns. The email may be written and signed in the same manner as the person you know. Obviously, this is intentional and strengthens the likelihood of the individual being deceived. One common tactic used by scammers is to request that you reset your company’s email password. Meanwhile, the link in the message sends them to a fraudulent page where the attacker has the opportunity to steal their credentials.
Tips to Avoid Being Scammed
Scammers use social engineering tactics to manipulate the victim’s emotions and lure them into their trap. Evoking curiosity, fear, and anger are tools of the trade that allow them to take advantage of a careless or unsuspecting individual. Therefore, exercise an abundance of caution if you receive a troublesome email, are drawn to an offer on a website, or are asked to open a seemingly important file. You can defend yourself against the majority of social engineering attempts that occur online by being vigilant.
In addition, the following advice will help you avoid most social engineering scams.

Never open attachments or emails from unknown sources. You are not required to respond to emails from senders you don’t know. Cross-check and confirm any communications from other sources. This may be done over the phone or directly from a service provider’s website, e.g. banks, credit unions, credit card companies, and any account that has your PII or financial information. Equally important, do this whenever you have the slightest suspicion about the content of the message. Keep in mind that familiar email addresses can easily be spoofed by a scammer. Emails that appear to be from a reliable source might have been sent by someone trying to steal your PII.
Use multifactor authentication. User credentials are one of the most important pieces of information that attackers look for. In an event where your PII is compromised, multifactor authentication helps to safeguard the security of your account. Otherwise, you’ll be at the mercy of the one who has stolen your credentials.
Be skeptical of alluring offers. As the saying goes, “if an offer seems too good to be true, it probably is.” For this reason, consider your actions carefully before engaging in any way. Often times, you can research whether you’re dealing with a genuine offer or a scam by a simple Google search. Another resource is the Global Scam Database.
Update your antivirus and antimalware programs. Make sure automatic updates are turned on. Likewise, establish a routine to download the most recent updates when automatic updates are not an option. Verify that the updates have been installed. Most importantly, always schedule system scans to look for any viruses or malware infections.
SUURV Technologies uses industry-leading software to train employees to detect all types of scammer activity. Bottom line, cybersecurity training is critical for every business. You would be surprised to find out how cost-effective it is to safeguard your business from data breaches, scammer attacks, and social engineering campaigns. Please contact us for more information, or call 210-874-5900.
Get Help Now!
We bring a laser focus to the three most critical functions of your company.
1. Business Operations

SUURV would love to talk with you about our vCIO and TAM support. It's the solution you've been searching for.
2. IT Infrastructure

THERE'S NEVER a one-size-fits-all approach. We implement custom solutions that scale with your growth.
3. Employee Support

You spent a lot of time building your team. We work around the clock to support them.